Disclaimer: Opinions expressed are solely my own and do not reflect the views or opinions of my employer or any other affiliated entities. Any sponsored content featured on this blog is independent and does not imply endorsement by, nor relationship with, my employer or affiliated organisations.
We've all been chasing the 'single pane of glass' for what feels like forever, right? Another dashboard, another so-called 'solution.' I've been digging into some tech lately MCP, A2A, and AG-UI ,and honestly, it looks like we might finally have the tools to build this thing ourselves. Imagine that.
How I see it is that MCP and A2A will help us fix the integration problem. For a long time, this has been (and still is) a painful process: going through API documentation, building integrations (or requesting one and waiting for a year to get it implemented, or even worse, the vendor tells you they have a voting system, meaning it will never get implemented if none of the big customers want it). And even if you build it, the second challenge is maintaining it; the more API actions you use, the harder it is to maintain.
So, let’s break down what each of these technologies means and how they can contribute to a more unified and intelligent SecOps environment.
Quick Refresher: What Are AI Agents?
An AI agent (or more technically, a group of cooperating, task-specific AI agents) is an intelligent system powered by artificial intelligence, particularly large language models (LLMs), designed to perform specific tasks autonomously or semi-autonomously. Within security operations, these agents significantly enhance the SOC team's efficiency by automating repetitive tasks, augmenting human decision-making, and ensuring consistent, rapid responses to threats. Currently, many of the Agentic AI solutions (also known as Agentic AI SOC Analysts) are focused on automating alert triage and investigation, specifically around Tier 1/Tier 2 investigations.
As previously discussed in our detailed exploration of SOC AI agents, we outlined four main categories tailored to cybersecurity operations:
Tool-Using Agents: Combining LLM reasoning capabilities with external tool integration (e.g., APIs, SIEMs, EDR platforms). They function as "smart SOC assistants" that handle data retrieval, enrichment, and automated actions.
Reasoning Agents (ReAct, Chain-of-Thought): These agents explicitly outline their reasoning steps, enhancing transparency and trust in decision-making, critical for compliance-heavy environments.
Memory-Enhanced Agents: Equipped with memory capabilities, these agents learn from historical alerts, patterns, and analyst feedback, progressively refining their contextual awareness and reducing redundant analysis.
Agentic RAG (Retrieval-Augmented Generation + Autonomy): Advanced agents that autonomously retrieve and synthesise diverse data sources, perfect for complex investigations where multiple context points are essential.
This edition is sponsored by BlinkOps
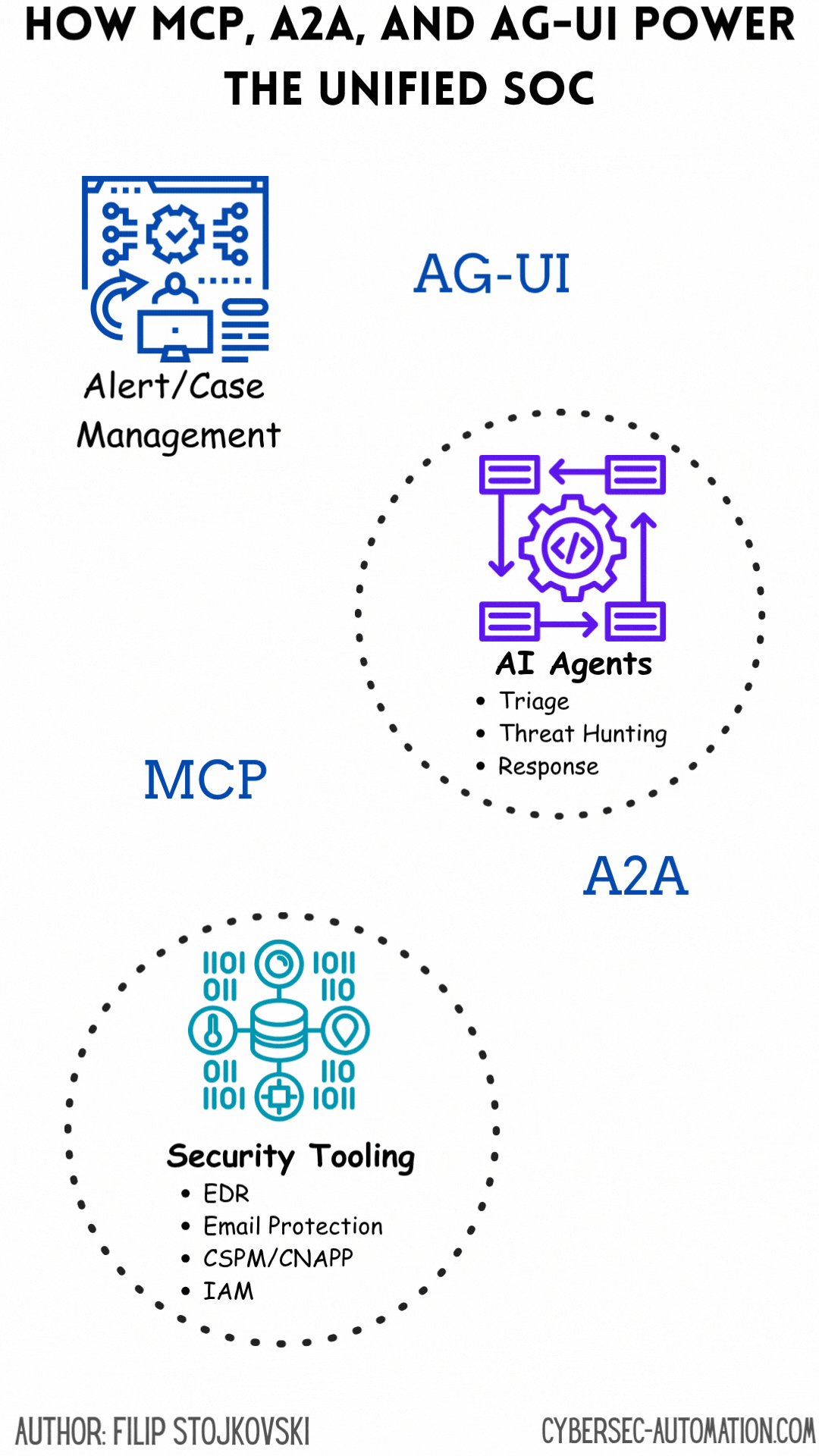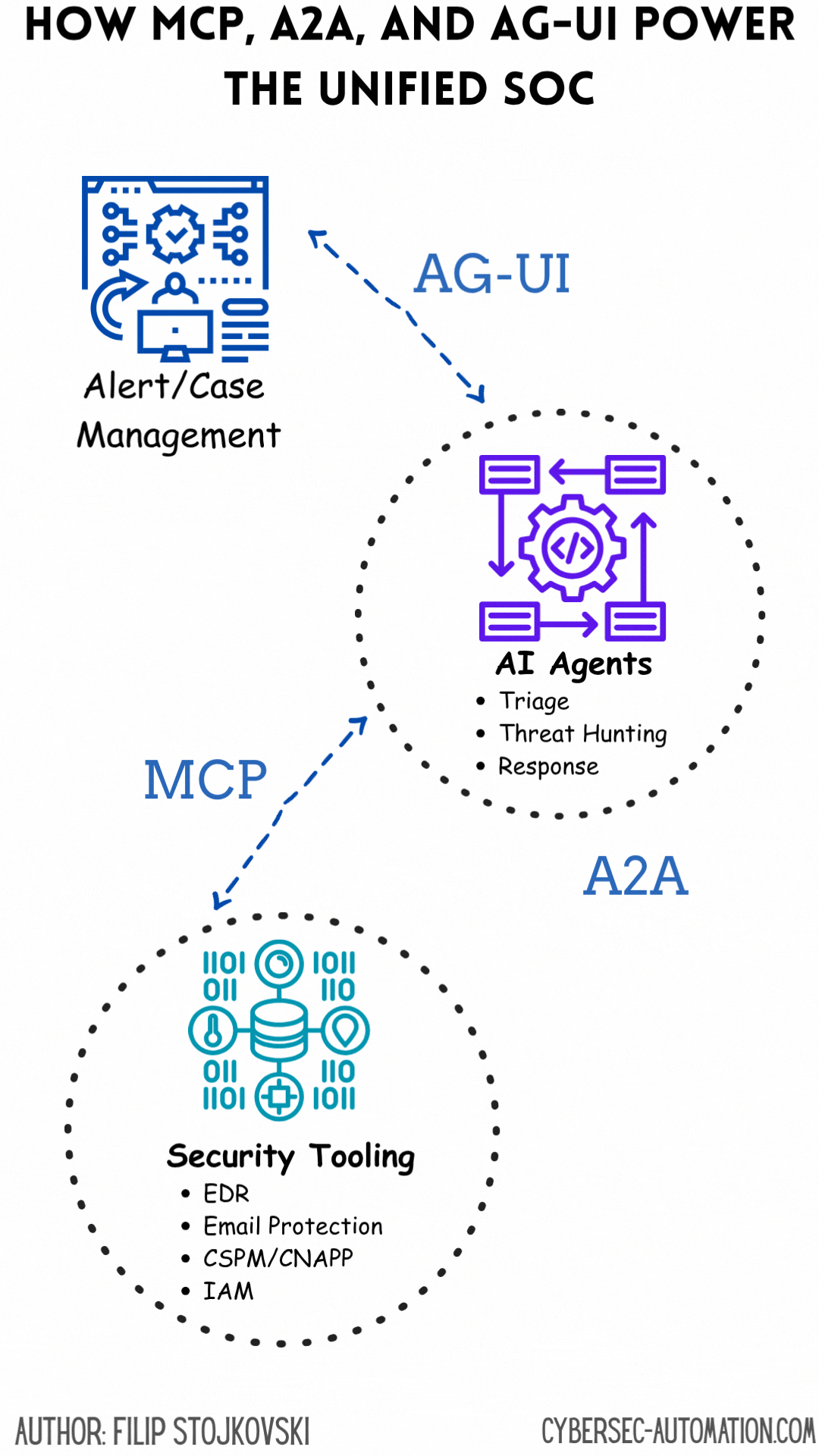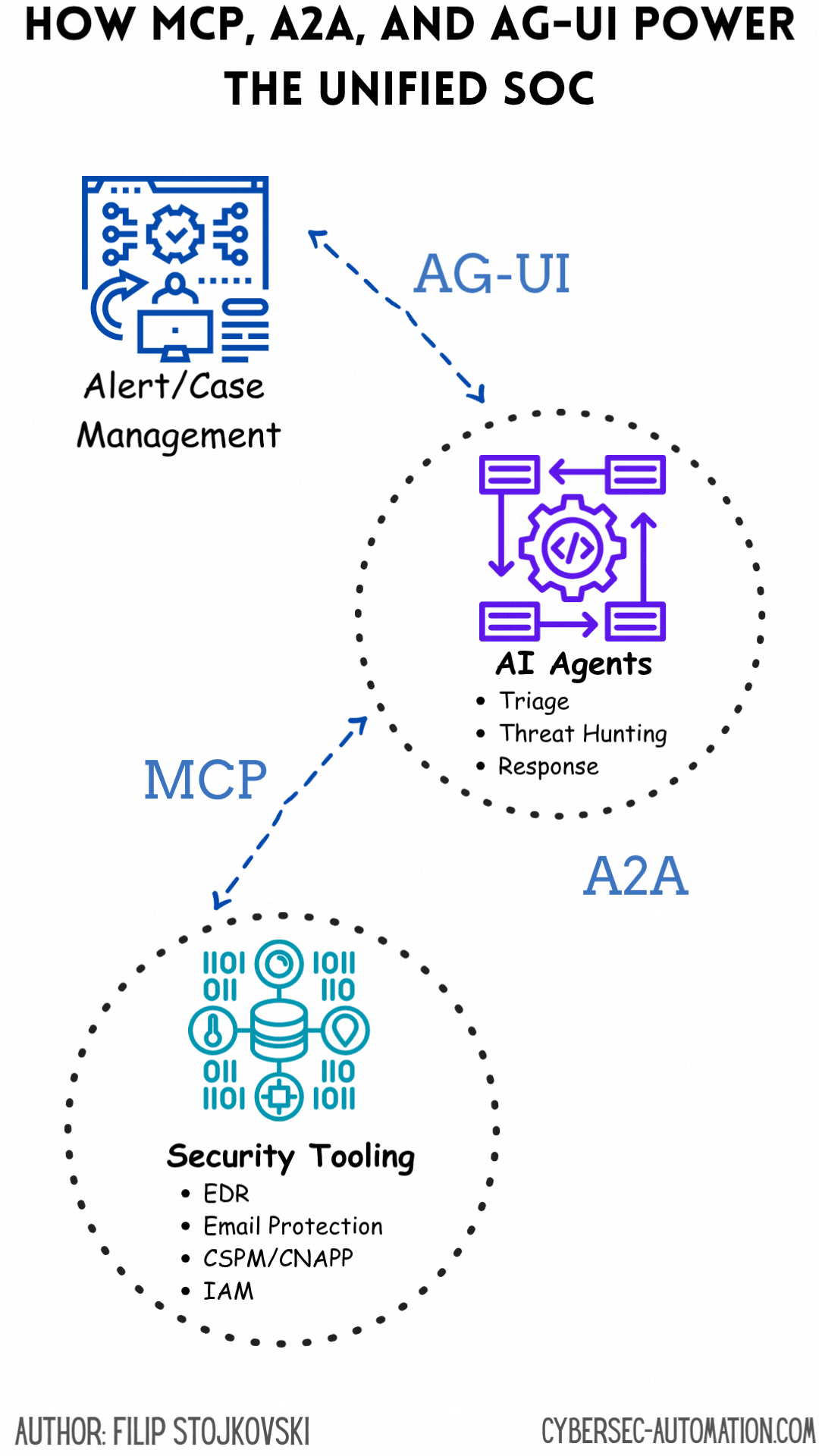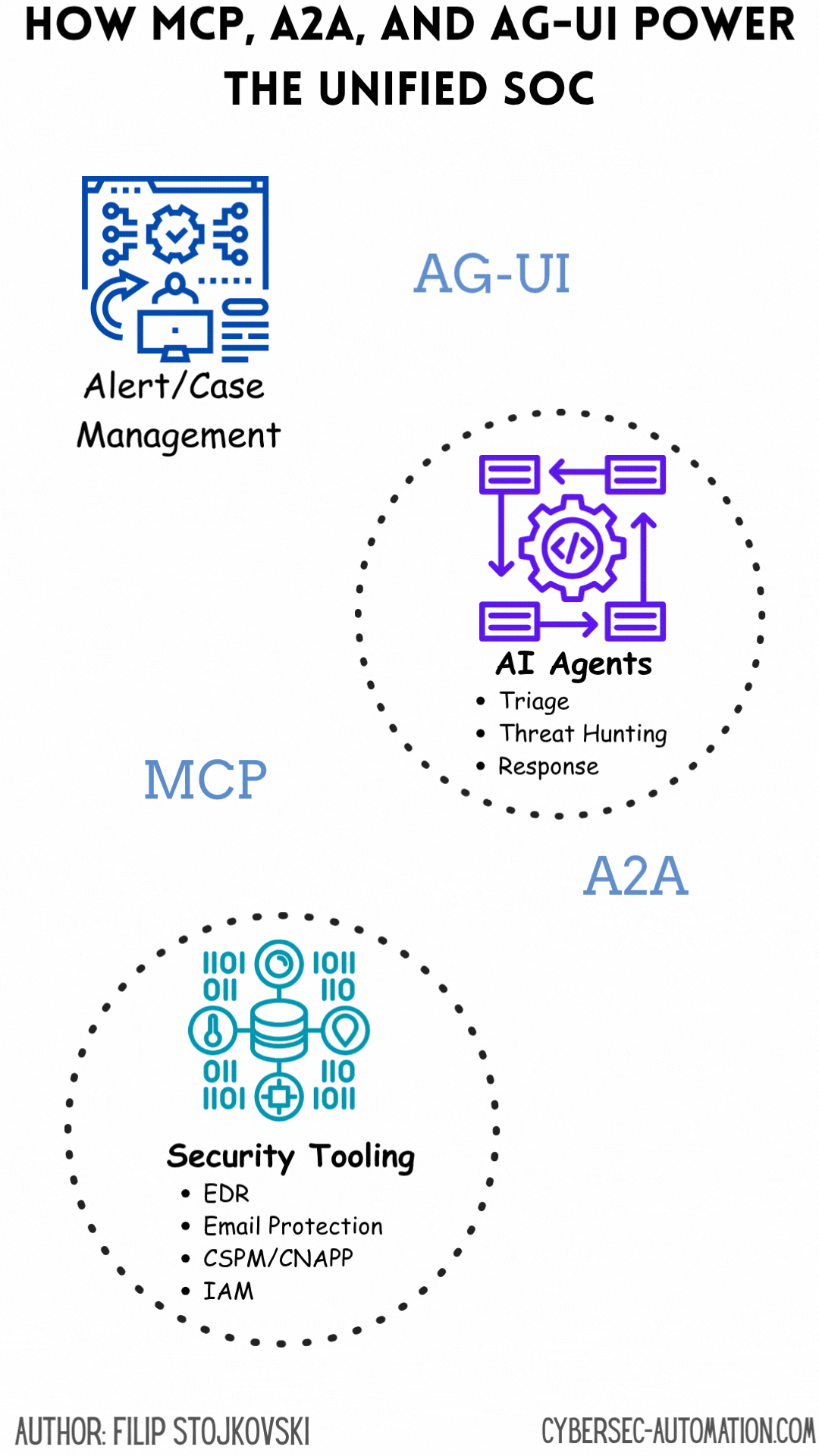
Decoding the Building Blocks: MCP, A2A, and AG-UI
To understand their collective potential, let's first define each component:
1. MCP (Model Context Protocol): Standardising Agent-Tool Interaction
Definition: MCP, in the context we're discussing, refers to Model Context Protocol. This is not to be confused with other "MCP" acronyms like Mission Control Platform. Model Context Protocol is designed to standardise how AI models, particularly Large Language Models (LLMs), interact with external tools, APIs, and data sources. Think of it as a universal adapter that allows an AI agent to seamlessly "plug into" various tools it needs to perform tasks. It often uses standards like JSON-RPC 2.0 and enables an LLM to be "fed" context or call a tool by providing a structured way to define tool capabilities and exchange information.
How it helps SecOps: In cybersecurity, an AI agent equipped with MCP could:
Reliably query a threat intelligence platform for the latest on an indicator.
Instruct a vulnerability scanner to perform a specific scan and retrieve the results in a usable format.
Interact with a SIEM or SOAR platform's API to fetch additional logs or trigger a predefined response action.
Gather context from diverse security tools without needing bespoke, brittle integrations for each one. This directly addresses the integration pain points mentioned earlier, as it aims to provide a consistent method for AI to access tool functionalities.
2. A2A (Agent-to-Agent Communication): Enabling Collaborative AI
Definition: A2A communication establishes a common language and protocol for different AI agents to discover each other, negotiate tasks, share information and context, and collaborate to achieve common goals. This allows for the creation of multi-agent systems where specialized agents can work together, even if they are developed by different vendors or for different primary purposes. These protocols often ensure secure and structured data exchange, supporting features like context passing, stateful interactions, and permission controls.
How it helps SecOps: A2A is crucial for building a truly intelligent and autonomous SOC. Imagine:
A "Triage Agent" that performs initial alert enrichment could use A2A to pass its findings to a specialised "Reactive Threat Hunting Agent".
The Threat Hunting Agent, after uncovering deeper threats by querying various tools (potentially via MCP), could use A2A to coordinate with a "Response AI Agent" to execute containment actions like isolating a host or blocking an IP address.
Different agents specialising in IOC enrichment, asset context, and malware analysis could share their findings in real-time to build a comprehensive understanding of an incident much faster than a human analyst working alone or a monolithic automation script.
3. AG-UI (Agentic User Interface): Crafting the Human-AI Partnership
Definition: An Agentic User Interface (AG-UI) facilitates natural and effective interaction between human users and AI agents (or systems of AI agents). Instead of just a dashboard displaying data, an AG-UI allows users to converse with agents, delegate tasks using natural language, receive proactive suggestions, and understand the reasoning behind agent decisions and actions. It's about creating a collaborative workspace where humans and AI can augment each other's capabilities. It focuses on explainability, interactivity, and allowing users to supervise and guide AI agents effectively.
How it helps SecOps: This is where the "single pane of glass" vision truly comes to life:
SOC analysts could interact with a suite of security agents through a unified, conversational interface. Instead of manually querying multiple tools, they could ask: "What's the latest on the phishing attempt from this morning? Has the source been blocked, and have we seen similar attempts?"
The AG-UI could present a consolidated view of an incident, not just raw data, but a narrative pieced together by collaborating agents, showing the steps taken, the rationale, and proposed next actions. Analysts could then approve, modify, or query these actions.
It can help demystify complex AI processes by providing transparency into agent operations , building trust and enabling analysts to effectively supervise AI-driven tasks.
The Convergence: Towards an Intelligent, Unified SOC
The real magic happens when MCP, A2A, and AG-UI work in concert:
MCP handles the "how" of tool use: It allows individual agents to reliably interact with the diverse set of security tools in the SOC's arsenal – from EDRs and firewalls to threat intel feeds and vulnerability scanners. This solves the fundamental integration challenge.
A2A manages the "who" and "what" of collaboration: It enables these specialized agents, each proficient with certain tools via MCP, to communicate their findings, share context, and coordinate complex workflows. For instance, an "IOC Enrichment Agent" uses MCP to query VirusTotal, then uses A2A to share the results with a "Timeline Analysis Agent" and an "Incident Coordinator Agent".
AG-UI provides the "where" and "why" for human oversight: It offers a centralized interface where human analysts can understand the bigger picture assembled by these collaborating agents, drill down into specifics, provide judgment, and steer the overall response. This makes the advanced automation accessible and trustworthy.
This combination directly tackles the desire for a "single pane of glass" not by just aggregating dashboards, but by creating an interactive, intelligent system that automates much of the underlying data gathering, correlation, and even decision-making, while keeping humans firmly in the loop for critical judgment and strategic oversight.
Analogy to Human SOC Teams:
Think about how a human SOC team operates:
Analysts have their specialized tools (SIEM, EDR console, TI portal) – MCP ensures AI agents can also use their "tools."
Analysts communicate with each other during an investigation (e.g., a Tier 1 analyst escalates to Tier 2, who consults a malware specialist) – A2A enables AI agents to have similar collaborative dialogues.
The SOC manager or lead analyst has an overall view, receives summaries, and makes critical decisions – AG-UI aims to provide this interactive, supervisory layer for human operators overseeing AI agents.
Practical Implications for Security Automation
Integrating AI agents using this trifecta can move SecOps beyond rigid, rule-based playbooks towards more adaptive, context-aware automation.
Reduced Integration Burden: MCP’s standardized approach to tool interaction could significantly cut down the time and effort spent building and maintaining custom integrations for every new tool or API change.
Smarter Enrichment: Instead of a 10-step enrichment playbook that often breaks , an agent (or a team of agents using MCP and A2A) can dynamically figure out what data it needs, fetch it from various sources, and synthesize a much richer contextual picture.
Dynamic Triage and Prioritization: A "Triage Classifier Agent" could use learned patterns and real-time context (gathered via MCP and shared via A2A with other intelligence agents) to more accurately prioritize alerts, reducing alert fatigue.
Automated Threat Hunting Loops: A "Reactive Threat Hunting Agent" could be triggered by a high-confidence alert, use MCP to query historical data across multiple platforms, identify patterns, and even suggest new detection rules or areas for proactive hunting, all while informing the human analyst via the AG-UI.
Streamlined Incident Response: From initial detection and enrichment through investigation, containment, and eradication, different AI agents can take on specialized tasks, coordinating via A2A and presenting a unified view and control points to human responders through the AG-UI. This is evident in the blueprint discussed for AI agents handling alert reception, reactive threat hunting, and response actions.
The Challenges Ahead
While the vision is compelling, it's not without hurdles:
Standardisation: The success of MCP and A2A relies on widespread adoption of common standards. While initiatives exist, achieving industry-wide consensus takes time.
Security of the Agents Themselves: If agents can take action, they become targets. Securing the agents, their communication (A2A), and their tool interactions (MCP) is paramount. This includes addressing risks like data leakage, unauthorised tool access, and potential manipulation of agent decision-making.
Complexity: Building, managing, and debugging systems of interconnected, autonomous agents can be complex.
Trust and Transparency: Analysts need to trust these systems. AG-UIs must be designed to provide transparency into agent reasoning and actions ("opaque decisions" are a major pitfall ), and robust guardrails and human oversight mechanisms are crucial.
Training and Cultural Shift: SOC teams need to be trained not just on new tools, but on how to collaborate effectively with AI teammates. This involves teaching prompting, delegation, and supervision skills.
Final Thoughts: The “Build or Buy” Moment for SecOps
The potential here is massive. For the first time, it feels like we have the right building blocks MCP, A2A, and AG-UI to finally crack the integration and automation problem without just adding another layer of complexity. The conversation is shifting from "if" we can automate to "how" we do it intelligently.
This brings every SecOps team to a crossroads: do you start piecing these technologies together yourself, or do you look for a platform that has already harnessed this power?
Building it in-house gives you ultimate control, but it's a heavy lift. On the other hand, a new breed of security automation platforms is emerging that's built on these very agentic principles. They offer a way to get the power of AI agents without the massive R&D effort, giving teams a launchpad into AI-first SecOps.
The key takeaway is that you're no longer stuck with the old, rigid playbooks of the past. Whether you build or buy, the future of the SOC is intelligent, adaptive, and agent-driven.
Have opinion on this, join the discussion here!
Vendor Spotlight: BlinkOps
BlinkOps is a modern security automation platform purpose-built for teams looking to deploy AI-driven workflows without drowning in code. The platform combines low-code flexibility with the intelligence of AI agents, giving security teams a way to automate repetitive tasks while staying adaptable to real-world changes.
What makes BlinkOps stand out is its approach to agents. Instead of chaining rigid steps like in traditional playbooks, you assign goals, define context, and BlinkOps agents handle the rest—enrichment, investigation, correlation, and escalation.
It's especially strong for SOC teams who want to:
Automate alert triage and incident response without writing complex scripts
Scale workflows across cloud, endpoint, identity, and email tools
Customise logic when needed but still launch fast with prebuilt templates
Whether you're modernising a legacy SOAR setup or starting fresh with AI-native tooling, BlinkOps gives you the structure of playbooks with the smarts of autonomous agents. Think of it as your bridge from rule-based automation to AI-first SecOps
🏷️ Blog Sponsorship
Want to sponsor a future edition of the Cybersecurity Automation Blog? Reach out to start the conversation. 🤝
🗓️ Request a Services Call
If you want to get on a call and have a discussion about security automation, you can book some time here
Join as a top supporter of our blog to get special access to the latest content and help keep our community going.
As an added benefit, each Ultimate Supporter will receive a link to the editable versions of the visuals used in our blog posts. This exclusive access allows you to customize and utilize these resources for your own projects and presentations.

